Everybody loves a good hacking because it spells doom for the target in question. In this case the target in question is Target. We’re going to delve into the financials and see that once again a hacking is no big deal.
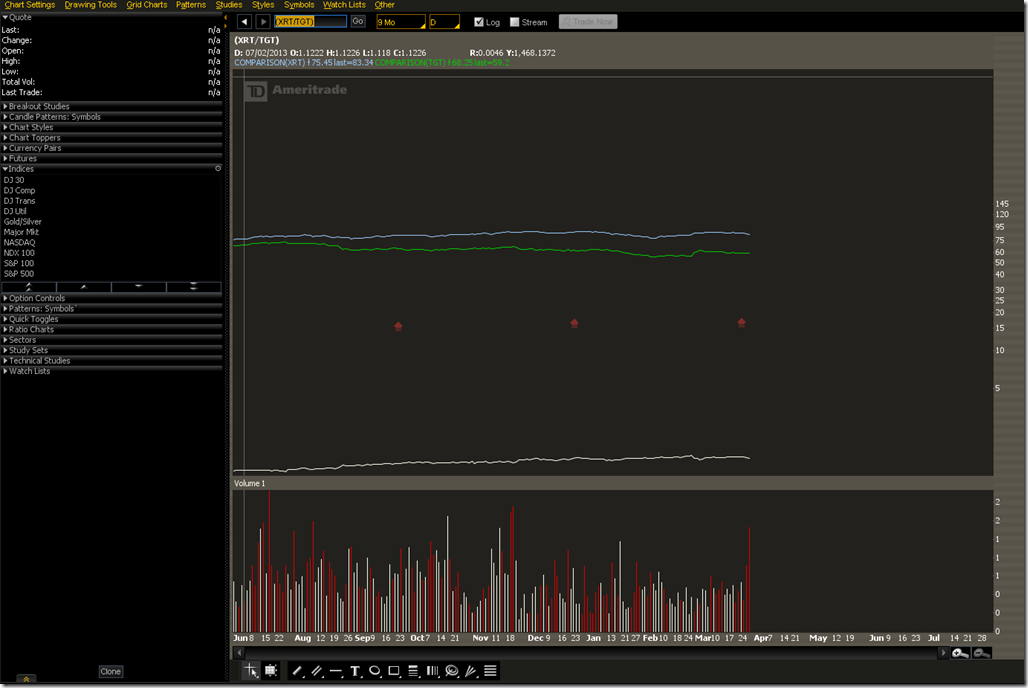
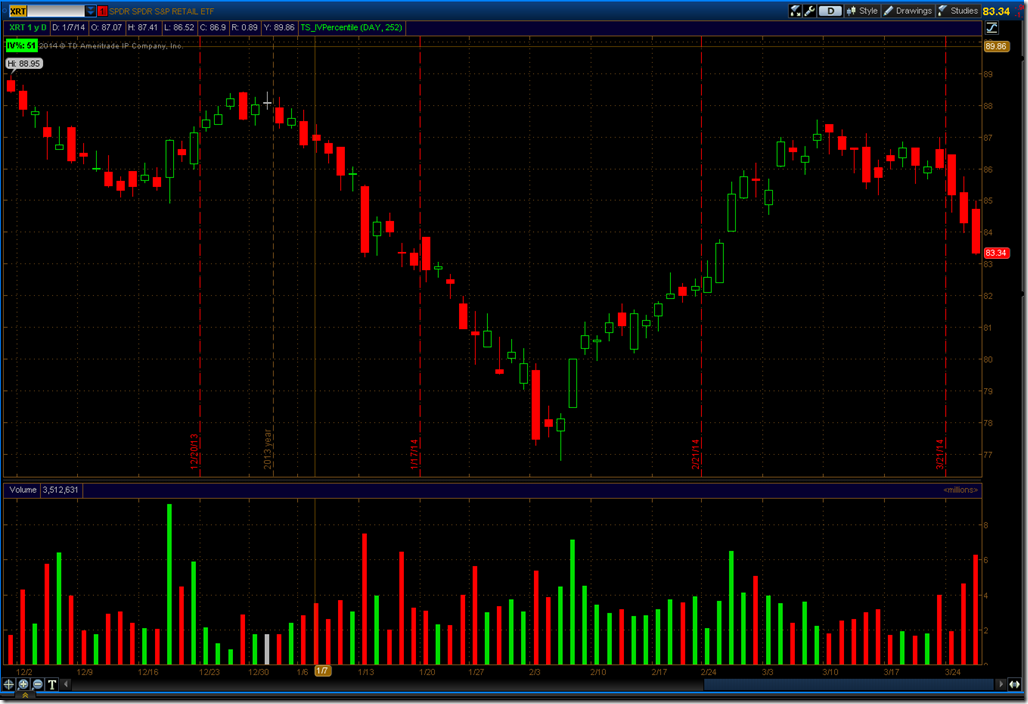
First we will compare Target (NYSE:TGT) (green line) to the SPDR Retail Sector ETF (NYSE:XRT) (blue line) so we can see the huge divergence between the retail sector as a whole and how poorly TGT has done since the hack. The first thing we notice is that TGT has under performed the bucket of other stocks that make up the retail sector. When picking single stocks vs. a broad ETF that is bound to happen. Next we notice that the ups and downs are about the same. This tells us that there’s no major comparative difference to the stock price during the time period when the breach was announced in September.
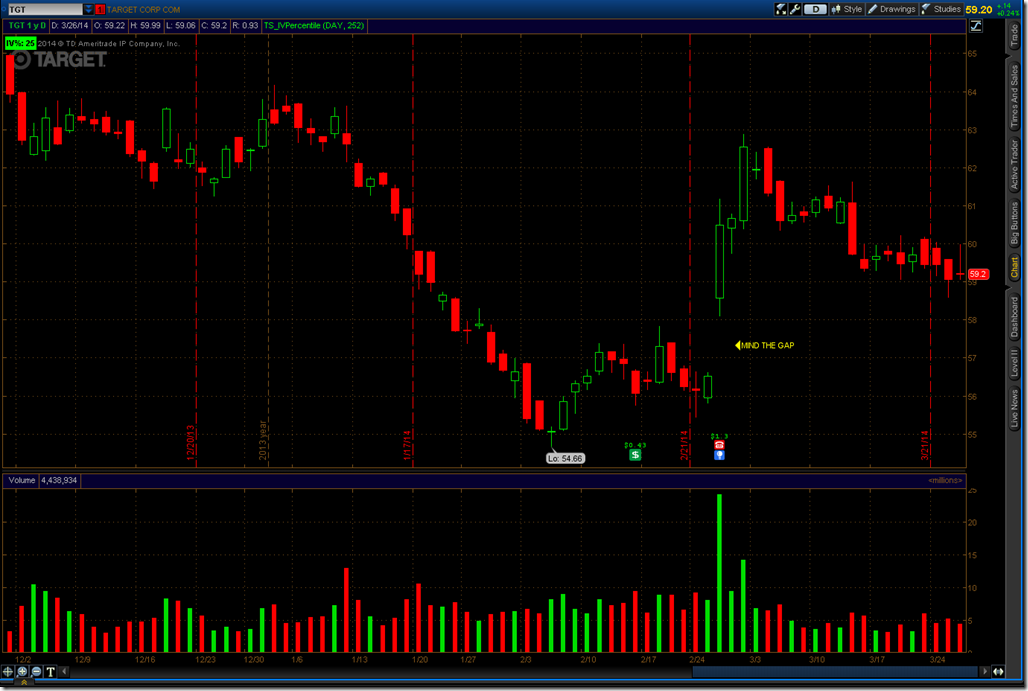
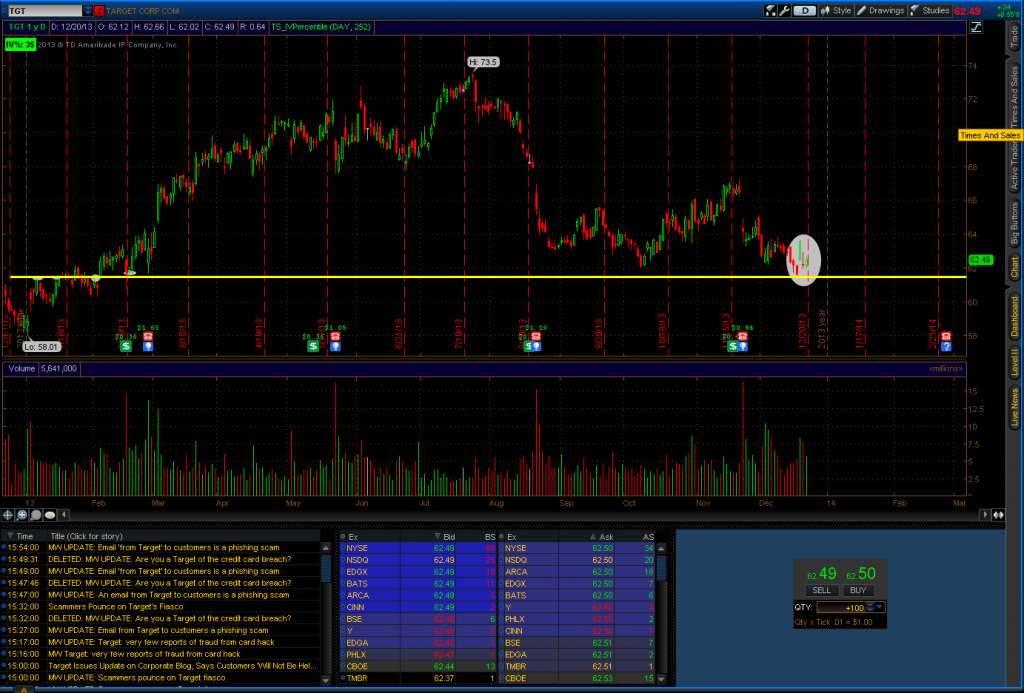
Next we’ll take a look at TGT during the December shopping season. Everyone in the infosec community jumped on the bandwagon that their sales were off because of the breach. Just look at that drop! It was obviously caused by the hackers, right?
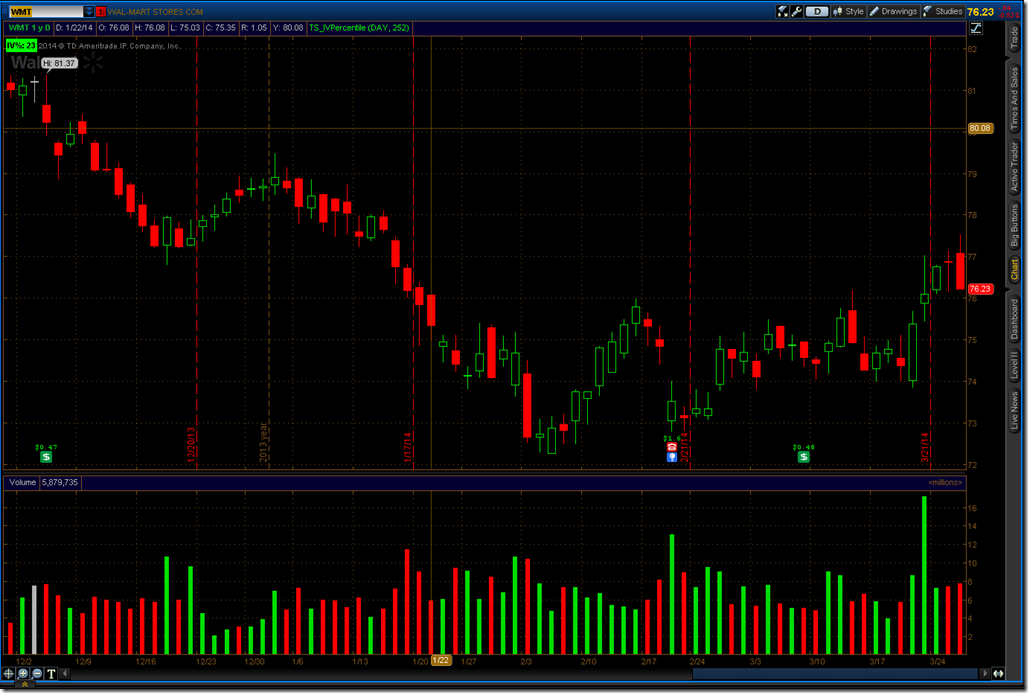
Wal-Mart (NYSE:WMT) must have the same problem if we look at December – January.
When we dig into XRT for the same time period we see an almost identical wave pattern. What this suggests is that everybody in retail had a rough winter, not just TGT.
The weather is why the entire retail sector is down. Well, every sector is down because of the weather. That’s the trendy thing that CEOs are blaming the bad Q4 and Q1 results on. Unless the hackers have a bot net that can control the weather we can attribute TGT and everyone else’s ills to the Polar Vortex.
The other thing that we need to consider that huge gap up when TGT announced earnings. That’s a 7% move in a single day. They posted 81 cents per share profit vs. 79 cents consensus. Revenue came in at $21.5B vs. consensus of $21.45B. In other words, Wall St. already accounted for the potential downside and priced it in. The impact was rather minor considering that they had incurred $61M in expenses but were covered by a $44M insurance policy for a net loss due to the breach of $17M. Yes, the impact is minor. We can tell this since the IV% in TGT is currently 25% while the IV% of XRT is 51%. There is a lot more concern over downside in the retail sector as a whole than there is in TGT.
Will consumer behavior change as a result of incidents like this? Unlikely. TGT made a brilliant move by having the We’re Sorry Save 10% This Saturday Sale the week of the breach. Many savvy consumers went shopping, your Dearest Leader included. Who can say no to a 10% off sale? Everyone I know walked away with a deal and no stolen numbers. Taking a gamble to get a deal is what you have to do. You have to buy in before they do. You have to buy the dip.
The thing security professionals and the writers at all the trade publications need to understand about consumer behavior is a sale is something that everyone in a bad economy will chase after. Most people have more than one credit card. They can always use a different card until a replacement arrives if the numbers are compromised. Consumers are not legally responsible for the bill if fraud does occur. That makes it the bank’s problem, and most people don’t care about the banks since that mess some of them caused with the housing market. What exactly is the tragedy that all of the industry publications are writing about? Either way the breach is the least of the bank’s worries, especially if your name is Citi.
Once again we have another data breach that causes a company to beat EPS, while life for everyone goes on. There is some economic impact, but it’s spread among insurance companies, card processors, issuing banks and retailers. The risk is shared among the sellers and the buyers have no risk at all. Everyone on Wall St. knows that these kind of incidents are nothing compared to disasters such as the Polar Vortex or a large oil spill in the Gulf of Mexico. Until the magnitude gets to be that large these events will be a nuisance rather than a disaster.
![TwCCloudSMBTrustinfoUS_Page[1]](http://dearestleader.me/wp-content/uploads/2013/06/TwCCloudSMBTrustinfoUS_Page1-71x300.png)