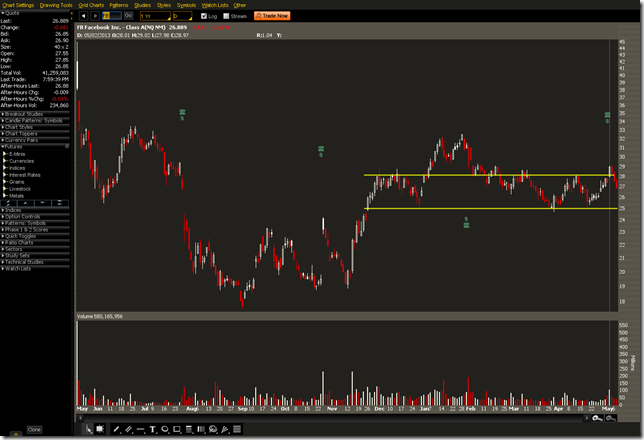
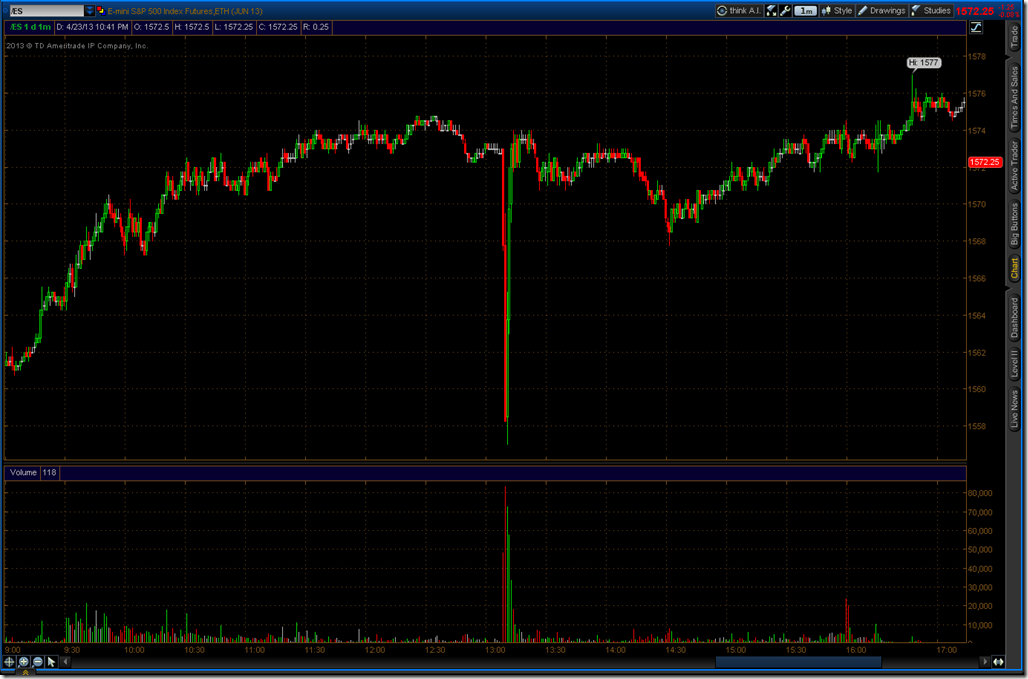
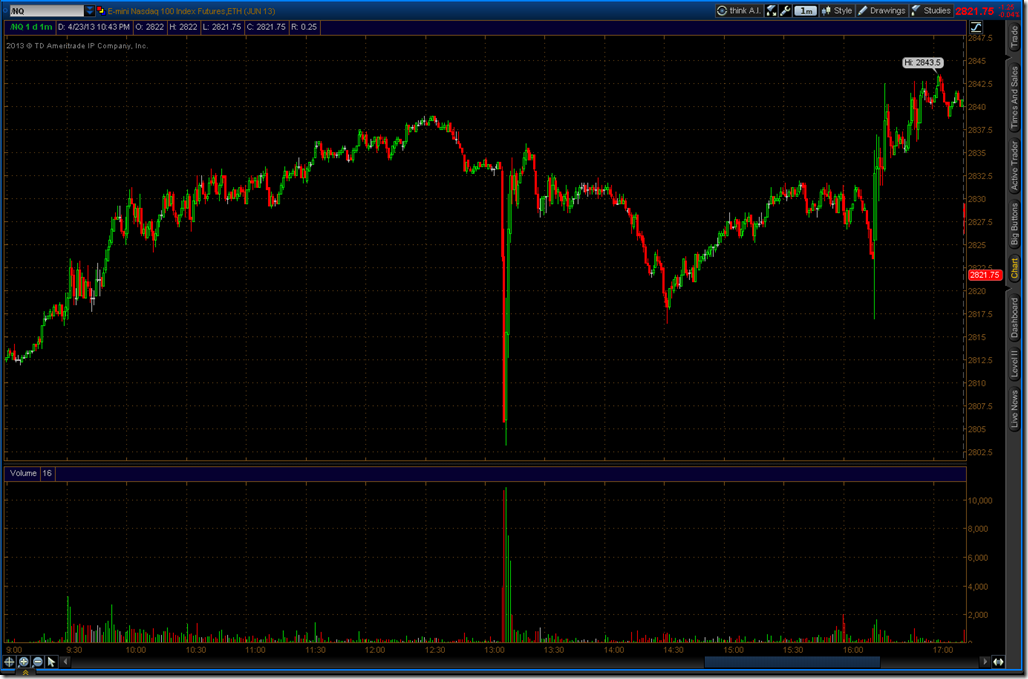
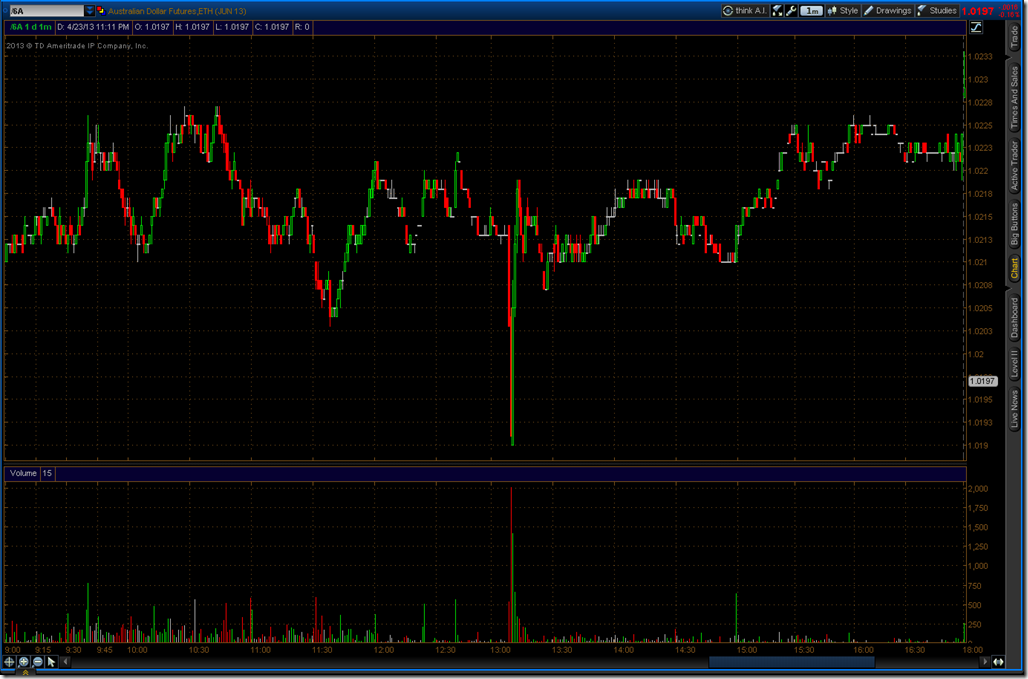
The activities of Mark Zuckerberg’s lobbying firm, FWD.us, has angered some liberal groups. Sellers have stepped in now that earnings are over and this may add a drop or two of fuel to the fire. If holds at $25 FB could be a long trade.
Tag: information security
Expected and Unexpected Market Events From AP Twitter Hack
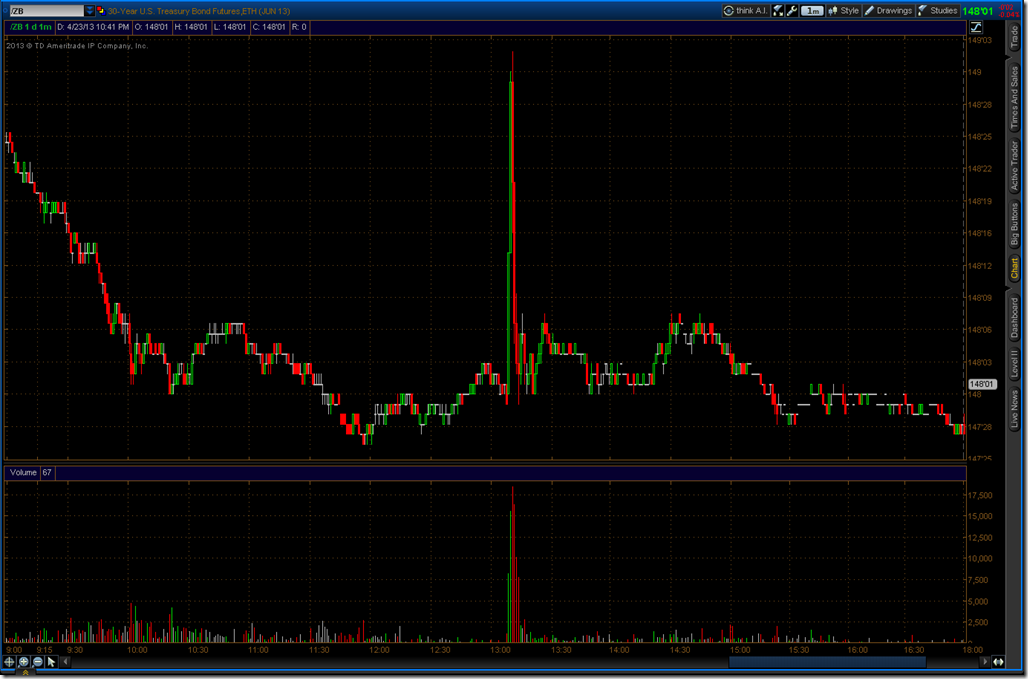
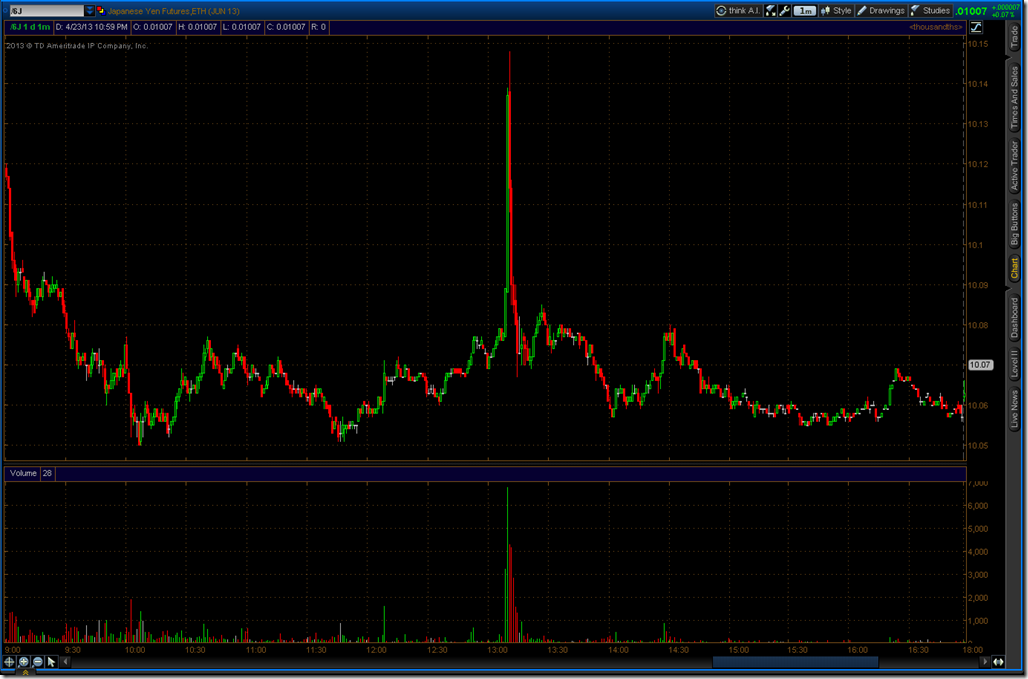
The AP Twitter hack created panic on Wall Street. We can look back to the LinkedIn breach and learn that security events can move markets in unexpected ways. As the media reported, all of the major stock indexes experienced a miniature flash crash. We can see this in the S&P and NASDAQ futures. According to Bloomberg, $136 billion in value was set on fire.
The reaction in other markets did not receive as much coverage, but were very interesting. The 30 year Treasury and the Japanese Yen had a near opposite reaction. This is very much like the buy it on a breach behavior that we saw with LinkedIn. Is it surprising Treasuries and the Japanese Yen turn out to be the place to go if something were to happen to The White House and the President and what does that say about the herd mentality? If we view the President as the CEO of the country, it seems a little strange to be buying the “stock” of a company that is in need of a new CEO. Perhaps the market is simply bullish on Joe Biden.
The Connection Between Employee Retention And Security
Security professionals are regularly informed that security should align to the business need. In most cases security professionals consider alignment to be meeting other business units half way or compromising on an issue. Another way to align to business need is to solve a non-security related problem for another department that has a beneficial outcome for security.
Cross training and personnel rotations can enhance your security program in addition to helping you meet some of the guidelines in ISO 27001/27002. Gaining support for personnel rotations for the sake of security is normally a difficult thing to win from management. What if it were possible to show that there is some business value to personnel rotations?
A recent WSJ article on big data reveals some interesting points about workers in certain industries that we should consider.
The bank gathered data on turnover, promotions, job changes and external pay to create a statistical model predicting why workers quit. Though the bank had used frequent pay raises to keep staff, the results showed that raising pay across the board by 10% might only shave a half point off the turnover rate.
Workers felt dissatisfied, not underpaid. More rapid job changes, even without promotions or corresponding rises in pay, made it much more likely that high-performing employees would stay, Mr. Nalbantian says.
Rather than sell personnel rotations as a security benefit to executives, we should partner with Human Resources to create a personnel rotation program that is designed to reduce turnover (thereby reducing the risk of disgruntled employees, or risks from hiring new employees) and increase job satisfaction. If HR gets executive support then it benefits security. It is also an opportunity to work closely with HR in designing the program. Any opportunity to take a break from APT, Cloud, DLP, and other BS Bingo phrases to establish better relationships with the business leadership could be a welcome change.
Personnel rotations by themselves have the benefit of potentially surfacing fraud or wrongdoing if proper observation and inspection are part of the program. The added benefit to personnel rotations is that the staff is now cross trained. That puts certain chapters of the business continuity plan ahead, such as the pandemic readiness portion. The complication of cross training personnel to be ready for the pandemic has already been taken care of.
These are some benefits to working with another part of the organization to help them to help us. HR can be a powerful ally in leading change. Giving them the encouragement and support can lead to positive security changes and recognition to the security team that goes out of their way to help another department look good.
LinkedIn data breach was $1M and a minor inconvenience
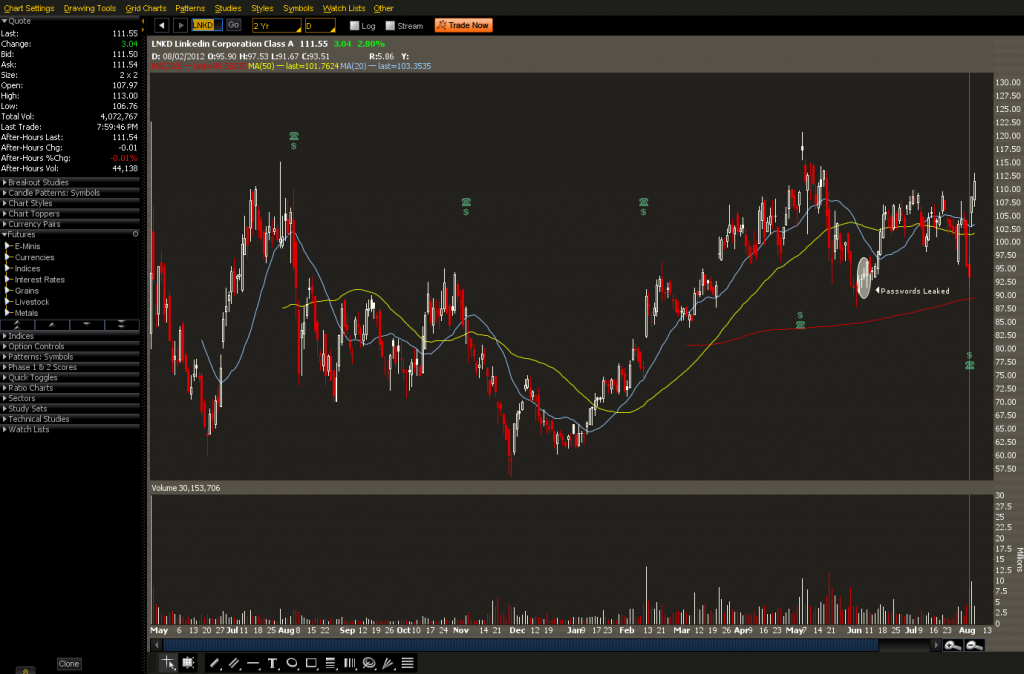
It hit the news today that the LinkedIn (NASDAQ: LNKD) data breach cost between $500K and $1M and that the company will be spending $2M-3M in the current quarter to enhance their security measures. In the larger picture this is a minor bump in the road. Revenue forecasts have been raised and on 8/2 they announced that top line growth came in at +89% at $228.2 million, beating analyst estimates of around $215 million. Bottom line income came in at $2.81 million down from 4.51 million in the prior year. The projected charge for security enhancements may affect next quarter’s earnings, but that doesn’t appear to be bothering anyone.
As we discussed earlier, in Security & Privacy Are Dead And Nobody Cares, investors do not care about minor security breaches. Sony and EMC suffered only in the short term. Blowing up an oil rig in the Gulf of Mexico seems to harm reputation more than having your corporate or customer secrets stolen. Revenue is what Wall Street and private equity are looking for. If the buying public doesn’t care, neither will The Street. With the economy in the state it is, and the move away from traditional job boards such as Monster World Wide, Inc (NYSE:MWW), LinkedIn will surely drive traffic, ad revenue, and premium subscriptions no matter what data they lose. We should consider the actual impact of the LinkedIn breach. Rather than running around screaming they were breached, what was breached should be considered. In this case passwords to users resumes were disclosed. Sure, someone could log in as that user and attempt to establish connections with other people for social engineering, etc. But from the user’s perspective the worst that could happen is someone could make their resume false, or simply delete it, which would mean they need to update their resume again. So in a way the hackers might have been helpful on some level, depending on who you are in the mix of all this. Yes, that is an oversimplification for the sake of drama, but ask most users and you will find LinkedIn is not a big deal to them, in many respects.
Technical Analysis
Much to the chagrin of security professionals LinkedIn experienced an uptick in their stock price the day the breach was announced. Why did this happen? People were logging in to change their passwords and were being exposed to advertising which increased revenue. The bankers felt that the stock was a buy on that news. No SecurID seeds were stolen, and no cute dolphins were drowning in oil, which means it’s a buy. After a nice earnings announcement LinkedIn is on its way back up and has broken out of the trading range it was in. There’s almost an 80% chance it will touch 115 which is a nice move from 92.50 prior to earnings. This isn’t the price action in a company that is going out of business because some passwords were leaked or because they’re spending a lot to improve their security.
What is worse than an Infosec breach?
In the scheme of things Infosec breaches are low impact events. Most companies recover in a few weeks. Quality problems can cost you even more. How does a software glitch that loses $450 million and reduces stock value by 80% sound compared to LinkedIn’s problems? There are larger things that can happen besides an Infosec breach that executives are worried about. Consumers are also worried about things other than security breaches. This is one reason why Infosec breaches have lower impact to a stock price than manufacturing or software errors, or accidentally serving up blackened crawfish in oil to gulf coast residents. Wall Street knows that a little bit of credit monitoring, and banks eating 100% of credit card and account fraud means that consumers will not change their behavior because someone else is paying for their choices. In economics we call this moral hazard, but that’s a topic for another time.
Preparing For The Next AMZN Cloud Outage
Amazon ($AMZN) made headlines over the weekend with the regional failure of AWS. We won’t go deep into the details of what happened or who was affected since that has been covered by many other outlets. In general, a incident caused loss of service in a particular region. The service providers were not able to deliver to their customers during the outage. While it is sexy to call it a cloud failure, the same end result could have occurred with any single site implementation. Hosting in your own data center, using the co-lo facility downtown, or an unfortunate GoDaddy location could cause your net presence to disappear.
Business leaders should evaluate what needs to be improved or changed in terms of resiliency. Decisions will need to be made based upon the size of your business and what your concerns are. A nano cap company (sub $50M market cap) will most likely have different requirements than a Large Cap global enterprise. Rather than invent the wheel, you can make use of frameworks to organize your activities. There are many out there, but today we will focus on ISO 27001 and ISO 22301.
Business Continuity is a component of ISO 27001, while ISO 22301 attempts to address Business Continuity as a whole. Section 4.2.1(d) of ISO 27001 requires that you identify the assets of the in scope portion of the business and the business owners of these assets, the threats to the assets, vulnerabilities that might be exploited by the threats, and the impacts to confidentiality integrity and availability.
Conducting a risk assessment in its most rudimentary form is a good exercise for any business of any size. The information that you put together as part of the risk assessment can be useful in other areas as well, such as obtaining the right insurance coverage at the right price. Fire or flood could impact your data center or it could impact manufacturing and logistics. Knowing this up front, you can take action to mitigate those risks or accept those risks.
Not everything needs to be corrected or addressed in some way, but having a running checklist of issues can be a good road map. A pizza restaurant with an online shopping cart may not care if the cloud provider of their online order application goes down. There’s always telephone, fax, and walk-in that will keep the business running. Cash flow, CapEx, OpEx, and other business drivers will influence the need for availability. Not every business will need multiple data centers if they are self-hosting or multiple availability zones in the cloud.
Scanlon Plans for Opportunity and Success
This week we continue our previous piece on HR Keywords for Growing Your Infosec Skills and Career. In our previous installment we examined some training and knowledge cultivating terms for increasing the value of their team or themselves. This week we will focus on another aspect of creating opportunity in your career, the Scanlon Plan.
Scanlon Plans are gain sharing programs where employees are rewarded for cost savings. This can be something as informal as placing ideas into a suggestion box, to company wide assigned areas for cost reduction or efficiency improvement on a recurring basis. If your company does not have a Scanlon Plan, then this is a great opportunity to bring it to the attention the executives in your organization. Who doesn’t want to hear about improved efficiencies, reduction in waste, and better margins? With a properly designed Scanlon Plan employees can receive financial rewards for making the organization more efficient. Who doesn’t want extra money?
How does this relate to Information Security or anything else? Do we really want to cut costs in our own area? Companies that implement Scanlon Plans as a suggestion box are looking for any way to save costs. This does not necessarily apply to your department, but the company as a whole. This can be an opportunity for Infosec personnel to help other departments find ways of cuttings costs. Working with other departments may be an “extra-curricular” activity to some supervisors; however, the importance of supporting the business should factor into middle management’s support for these programs.
Proactively working with other managers provides the opportunity to understand the business more, which will help Infosec personnel understand what is important to the business, and what needs to be protected. For example, working with manufacturing to reduce waste by implementing a recycling program can reduce costs which frees up capital for other purposes, such as information protection. Some of the scrap from the manufacturing process could be sold to a recycler, reducing the overall operating costs of the manufacturing operation. These savings are not only of interest to the manufacturing department, but it could be helping the goals of the Corporate Social Responsibility (CSR) department or program if one exists. This provides recognition from management, but can also help with improving security.
Another example involves finding something unrelated to Infosec that allows the VP of Operations to save money. That’s great! What if Infosec professionals approach him/her and offer to help them implement the changes that will save them money? In exchange for becoming the project manager and seeing the changes through to completion, the VP agrees to spend part of the savings on additional security measures. The VP of Operations gets a bonus for reducing their budget, the Infosec professional receives their bonus for a cost reducing idea, and security was improved during the process. A little barter was used in this scenario, but several end goals were accomplished.
This approach is a transition from employee to stakeholder. It offers opportunity for Infosec professionals to grow into GRC roles over time by helping the organization with its efficiency. Inefficient business processes are one Risk in GRC. By promoting process improvement and efficiency Infosec professionals go from the department that always says, “No!” to true stakeholders in the business. This gets us a seat at the executive table because we are involved in the business and we can demonstrate value by using our creativity to solve business problems. That alone can be a career changer or career booster.
Further Reading:
Human Resource Management 12th ed. Mondy
HR Keywords for Growing Your Infosec Skills and Career
There are different approaches to building skills for career advancement. Rather than focus on specific skills for Infosec, we will focus on creative approaches to Human Resources for developing skills. These ideas may also be useful to management in developing a team. The concepts can also be applied to other careers in addition to Infosec. We will be covering some terminology that may be useful when discussing career development with Human Resources professionals and potential ideas for implementing them. Depending on the organization Human Resources may or may not want to be directly involved in these ideas. The term workers refers to anyone performing work whether they are a contractor, part-time, full-time, or temporary.
Job Enlargement is the an easy step to growing an worker’s skills. Job enlargement consists of adding more tasks at the same level of responsibility. In the physical world teaching an employee how to operate multiple machines on a manufacturing floor is an example of job enlargement. In the IT field this could be adding/removing users from both Windows and Linux systems or supporting Mac and Windows desktops. Workers managing perimeter firewalls could be given responsibility to manage end point protection in addition to the single task they had previously.
Job Enrichment is different from job enlargement. Job enrichment involves increasing the responsibility that workers have, where job enlargement is adding tasks at the same level. This can be adding more difficult and complex tasks to an worker’s duties. This can also include delegating higher level duties by management. In these arrangements accountability would remain at the same level (management), but the worker would gain hands on experience by completing the task with management supervision. Additional technical skills can be acquired through job enrichment. On the job training for supervisor responsibility can also be accomplished through job enlargement.
Job Sharing is normally for part time positions where one worker may work 20 hours and another worker will do the some job for 20 hours making up 40 hours of productivity. Modifying job sharing for full time workers can also create growth opportunities. A worker can be given two distinct jobs and split a 40 hour week between the two jobs. This can occur under the same supervisor or employees can be shared among departments. One example is the financial auditor who has previous experience in IT audit. Rather than hiring a full time auditor for IT, the company may have the financial auditor do 10 hours of work in the IT department per week or as needed. Job sharing also allows workers to gain skills in a different line of work part time while continuing to perform their existing work tasks.
Job Rotation involves moving workers from position to position to broaden their skills. This is normally a full time reassignment rather than splitting time as with job sharing. Some security standards recommend job rotation to detect fraud, which can also be a benefit. This can be an area where Human Resources and Security can work together in justifying a formal job rotation program. This would guarantee opportunities to learn new skills from being moved from position to position. Job rotation and job sharing also can be part of a continuity of operations program where workers are cross trained to reduce impact to the business in the event of a disaster or someone simply departing the company.
Job Sculpting involves tailoring job descriptions to the skills, and talents, and interests of each employee. If a supervisor engages in job sculpting, employees will have customized job descriptions on an individual basis rather than a one size fits all approach. There are several steps that go into job sculpting that we won’t cover, but it does allow workers to put their other talents to use which can benefit the organization and the worker.
These concepts can be used by workers to gain additional skills and increase their marketability in the job market. Approaching supervisors or Human Resources with the desire to broaden skills is one way to shift your career into high gear. By being proactive and participating in job enlargement or any of the other career growth strategies Infosec professionals can expand their skills or discover new lines of work, such as project management, that relate to Infosec. Supervisors can also put these concepts to use in order to have workers back each other up through cross training and to help workers in developing themselves to serve the organization and the profession. In the coming weeks we will go over different ways of using these concepts to grow your skills and responsibilities.
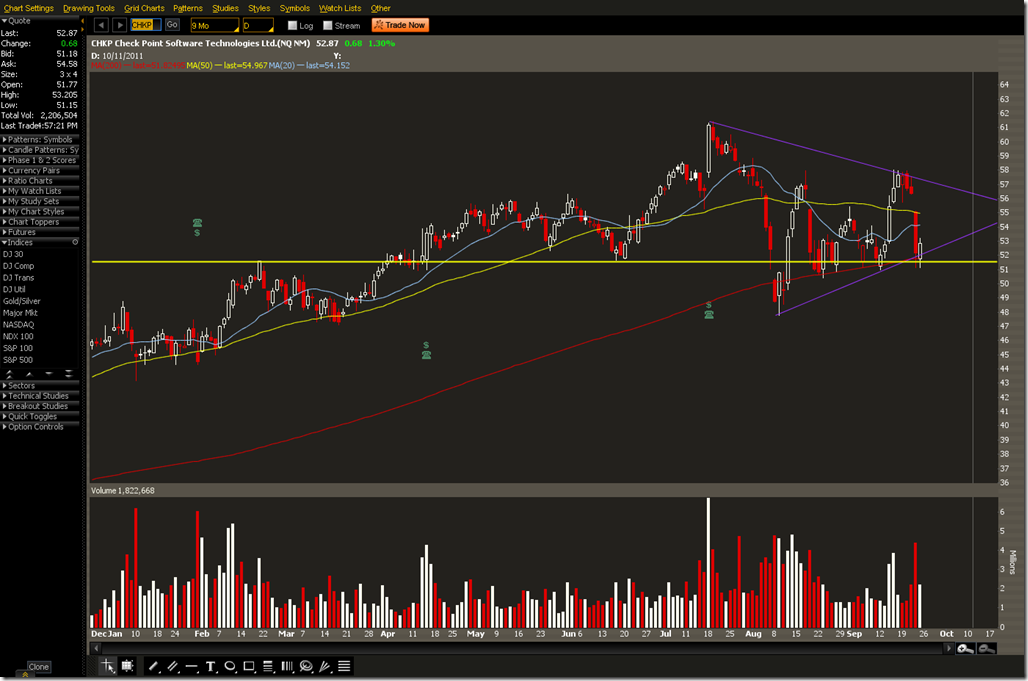
Checkpoint Trade CHKP
The well known maker of firewalls and other security solutions has a nice setup here. Prior resistance from February 18 held up as support at the 200 DMA. CHKP also closed back inside the trend line on the 23rd. Earnings is set for October 20 which would account for a big squeeze if the stock stays inside the triangle. The weekly trend is still up so this is likely to be a continuation.
Aside from playing long equity there are a few options here.
One is to sell an ATM Vertical option. This assumes that the 200MA, the February resistance, and the trend line will hold up. The 50MA was resistance on Thursday and that is relatively close to resistance on August 18 and also Near the end of April. Closing half a position close to the 50MA would be one way of reducing this exposure. This is the setup SELL -1 VERTICAL CHKP 100 OCT 11 52.5/50 PUT @.95 LMT
The other option is to bet on a break out after earnings on October 20. IV for October is 50% while November is 45%. A call calendar above the resistance at 58 could be one way to capture a break out. BUY +1 CALENDAR CHKP 100 NOV 11/OCT 11 60 CALL @.55 LMT
If we were looking to pin close to the center of the triangle BUY +1 CALENDAR CHKP 100 NOV 11/OCT 11 57.5 CALL @.73 LMT or BUY +1 CALENDAR CHKP 100 NOV 11/OCT 11 55 CALL @.85 LMT could also be good choices. These would be taken off close to expiration, but before earnings.
The Hartford to Offer Data Breach Insurance
Good news for small firms. The Hartford (NYSE: HIG)is now offering data breach insurance targeting small business. Insurance is a good control to invest in to supplement other information security controls or as the main control if your business is very small. Some E&O policies may also have riders that cover data breaches. If you own a business you should review all your policies to be sure that your coverage objectives are met.
Relying on insurance is a form of risk transference. The policy holder is transferring some of the risk in the form of impact costs to another party. This can be useful and could potentially save a small business from severe financial damage if it has to absorb the costs of investigating a breach or cover the cost of credit monitoring for its customers.
In trading terms buying a Put is the same as buying insurance. The purchaser is given the option to sell their investment for potentially more than the current market price. An unexpected oil spill or embezzling scandal could be the equivalent of intruders or dumpster divers getting their hands on your customer’s data.
There’s a very small range in HIG. There is support around 16 so this could be played different ways. Shorting the stock with a stop above the trend line is one option. The Oct 18/16 Bear Put Spread is going for .69 and has a max profit of 131. Since front month IV is higher than November a put calendar may be an alternative if you want to play the descending triangle pattern. The 16 Oct/Nov Put calendar is going for .47. There is a possibility the stock could drop to 12 if the descending triangle follows through.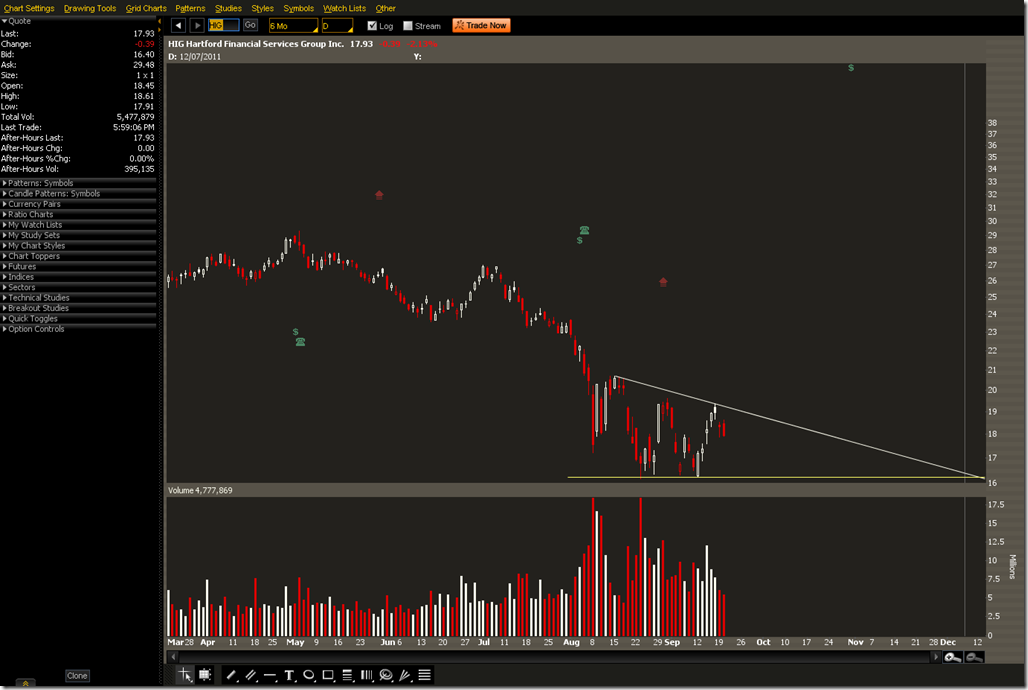
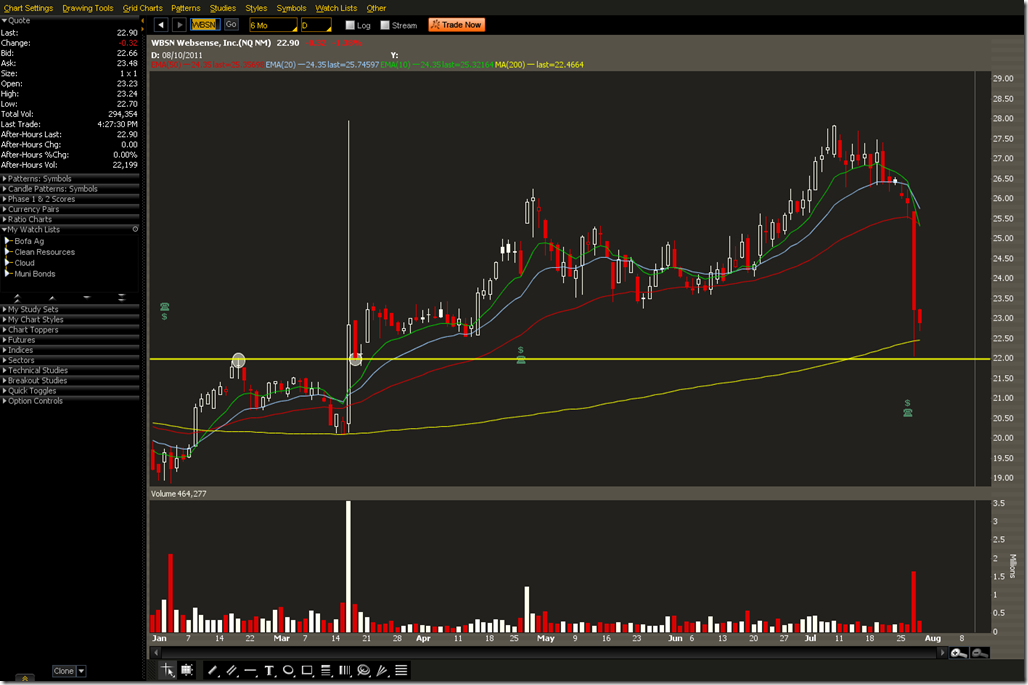
Websense misses EPS
Websense managed to stink up earnings. EPS posted was $0.35 actual vs. $0.38 estimated. Websense lost about 15% after earnings were announced.
The earnings call discussed “the new normal” of attacks being persistent and the “bad guys” wanting our corporate crown jewels. Fundamentally, we can assume that their sales and marketing force will be able to capitalize on the activities of groups such as Anonymous and LulzSec. They noted that they have increased sales of Triton products. Growth of 47% Year over Year $44.4M. 1st quarter Triton exceeded non-Triton billing. On the call Websense said they are clearly a Triton company as they look to the future. This still does not mean that we should be bullish on DLP technology, even though it is part of Triton. More than likely the bundle of Web, Email, and DLP will see Web and Email use, while the DLP sits on the shelf.
Since Websense is still above the 200MA and it held the 200MA back in March now may be a good time to get bullish, regardless of how well their technology works. There’s enough marketing hype to continue to propel them along.
The August 22.5/20 Bull Put Spread is currently pricing at $0.57. If it stays above 22.5 by August options expiration that would be a gain of 29.53%. Max loss per contract would be $193 vs. a max gain of $57. Volatility is high so selling options is a good idea here.
A bearish play would be to use the August/September 22.5 Put Calendar. This would be a debit of approximately $0.50 and would be a reasonable bearish bet since August Implied Volatility is higher than September. The Put Calendar may be a good play if we are feeling bearish about the overall market and US Debt Ceiling issues dragging everything down.